oauth tutorial - OAuth 1.0 vs OAuth 2.0 - oauth2 tutorial - oauth authentication
Oauth (1.0)
- In 2006 were no open standards for API access delegation. OAuth was designed to solve the application-to-application security problem. OAuth Core 1.0 was released in 2007.
Terms
- User, Consumer, Service Provider, Protected Resource, Provider API
5 parameters to work with OAuth 1.0
- Consumer
- key & Consumer secret
- Request token URL
- Authorize URL
- Access token URL
OAuth 1.0 components
- Token = Key + Secret Message = Document + Digital Signature Application = Consumer + Access toAPI
OAuth 1.0 Authentication Flow
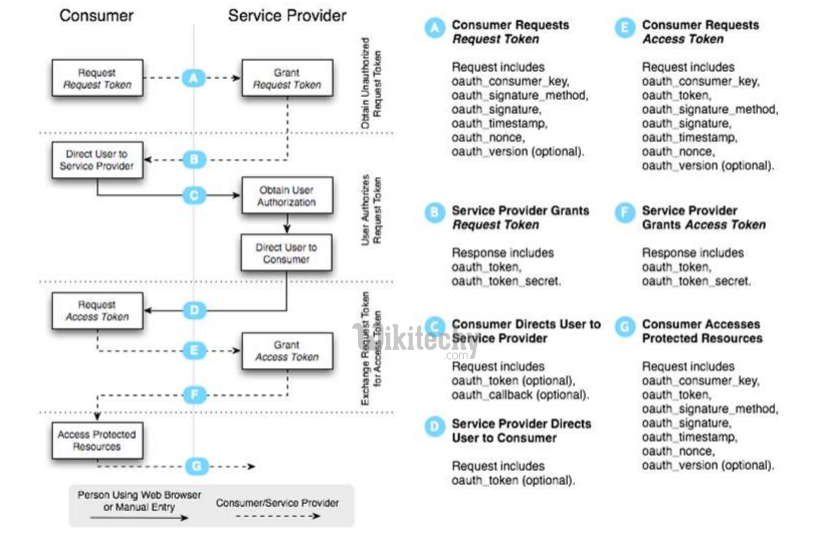
Learn OAuth - OAuth tutorial - OAuth 1.0 Authentication Flow - OAuth examples - OAuth programs
- OAuth 1.0 = Fetch Request Token + Redirect to Authorization + Fetch Access Token + Call API + Signature calculated with secret-key
OAuth 2.0
- OAuth 2.0 focuses on client developer simplicity while providing specific authorization flows for web applications, desktop applications, mobile phones, and living room devices. OAuth 2.0 is more a framework than it is a defined protocol. OAuth 2.0 is not backwards compatible with OAuth 1.0.
OAuth 1.0 vs OAuth 2.0
Problems of OAuth 1.0
- Authentication and Signatures on client side User Experience and Alternative Token Issuance Options Performance at Scale
OAuth 2.0 changes:
- OAuth 2.0 relies completely on SSL for some degree of confidentiality and server authentication. Cryptography-free option for authentication which is based on existing cookie authentication architecture. Simplified signatures Separation of Roles (SSO support) Short-lived tokens with Long-lived authorizations
OAuth 2.0 flows
- Web Server Flow – for clients that are part of a web server application, accessible via HTTP requests. This is a simpler version of the flow provided by OAuth 1.0.
- User-Agent Flow – for clients running inside a user-agent (browser).
- Device Flow – suitable for clients executing on limited devices, but where the end-user has separate access to a browser on another computer or device.
- Username and Password Flow – used in cases where the user trusts the client to handle its credentials. Client Credentials Flow (JWT) – the client uses its credentials to obtain an access token. This flow supports what is known as the 2legged scenario. Assertion Flow – the client presents an assertion such as a SAML assertion to the authorization server in exchange for an access token.
OAuth2 Web Server Flow
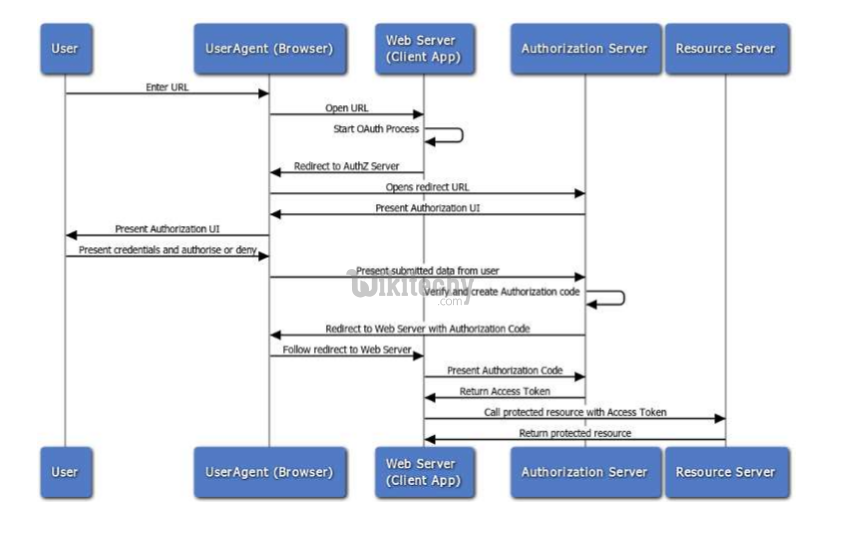
Learn OAuth - OAuth tutorial - oauth2 web server flow - OAuth examples - OAuth programs
SSO
- Particular case of Web Server Flow when Client App and Resource Server use the same Authorization Server
OAuth2 User Agent Flow
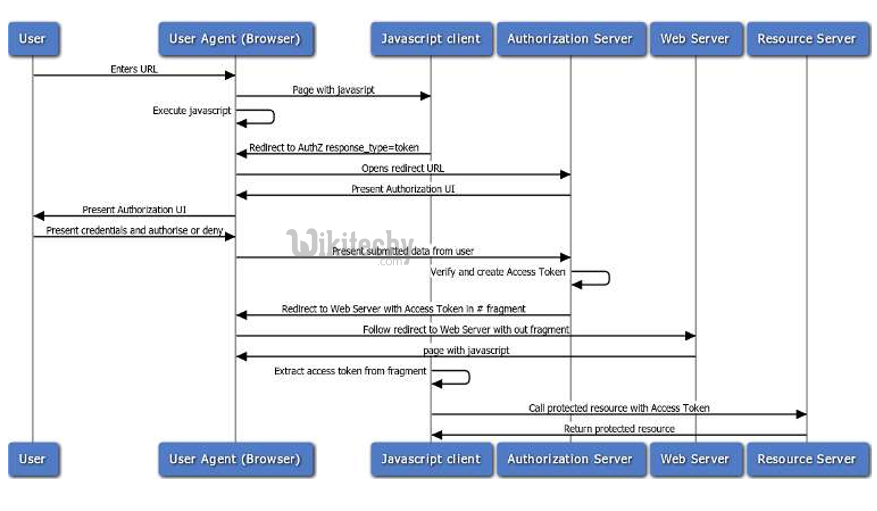
Learn OAuth - OAuth tutorial - oauth2 user agent flow - OAuth examples - OAuth programs
OAuth2 Resource Owner Password Credentian Flow
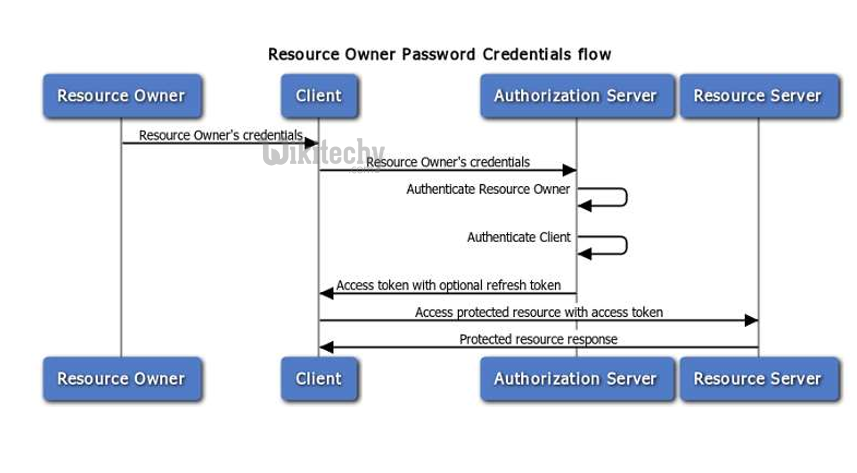
Learn OAuth - OAuth tutorial - oauth2 resource owner password credentian flow - OAuth examples - OAuth programs
Does OAuth1 better than OAuth2?
- No, they have different purpose: OAuth1 for server to server communication and OAuth2 for user/device to server
Does OAuth1 more secure than OAuth2?
- Yes and No
- OAuth 1.0 may be used without HTTPS
- But, OAuth2 same secure as SSL
When to use OAuth1 & OAuth2?
- OAuth 1.0 – server-to-server
- OAuth 2.0 – browser/device/client-toserver
