oauth tutorial - OAuth Accessing a Protected Resource - oauth2 tutorial - oauth authentication
How to access a Protected Resource in OAuth 2.0?
- The client provides an access token to the resource server to access the protected resources.
- The resource server must validate and verify that the access token is valid or not and check if it is not expired.
Hence, there are two standard tokens which are used for sending credentials and they are
Bearer Token
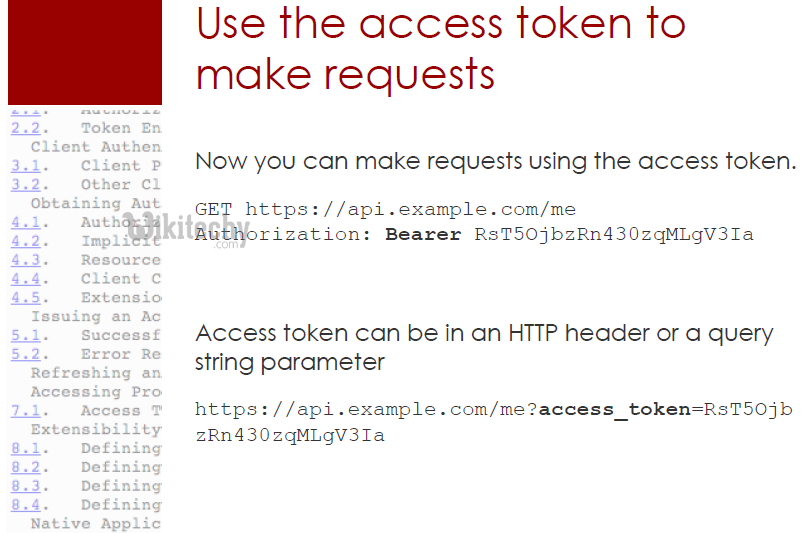
- The access token which can only be placed in POST request body or GET URL parameter as an option in the authorization HTTP header.
Authorization header
Authorization: Bearer [token-value]
click below button to copy the code. By - oauth tutorial - oauth2 tutorial - team
Example:
GET/resource/1 HTTP /1.1
Host: example.com
Authorization: Bearer abc...
click below button to copy the code. By - oauth tutorial - oauth2 tutorial - team
Message Authentication Code token
- A cryptographic Message Authentication Code (MAC) is computed using the elements of the request and is sent to the authorization header.
- After receiving the request, the MAC is compared and computed by the resource owner.
- The client has obtained the required token accessing the protected resource or web API is a matter of including the token in the HTTP request.
- The most common access token type is bearer and the second one is Message Authentication Code .
- The token is kept secure at all times, since the type will have access.
- The table which is given below shows the concepts of accessing the protected resource.
| Sr.No. | Concept & Description |
|---|---|
| 1 | Authenticated Requests
It is used to get the authorization code token for accessing the owner resources in the system. |
| 2 | The WWW-Authenticate Response Header
Field
The resource server includes the "WWW-Authenticate" response header field, if the protected resource request contains an invalid access token. |
Example request
- We need to set the authorization header which is a straightforward, and it should be possible with any HTTP client / library which are used.
- Some of the example request are given below:
With CURL
curl -H "Authorization: Bearer $ACCESS_TOKEN" URI
click below button to copy the code. By - oauth tutorial - oauth2 tutorial - team
With java.net.URL
import java.net.*;
import com.nimbusds.oauth2.sdk.token.*;
// The obtained access token
AccessToken accessToken = ...
// The protected resource / web API
URL resourceURL = new URL("http://example.com/resource/1");
// Open the connection and include the token
URLConnection conn = resourceURL.openConnection();
conn.setRequestProperty("Authorization", accessToken.toAuthorizationHeader());
// Continue...
click below button to copy the code. By - oauth tutorial - oauth2 tutorial - team
With JAX-RS Jersey client
import javax.ws.rs.client.*;
import com.nimbusds.oauth2.sdk.token.*;
// The obtained access token
AccessToken accessToken = ...
Invocation.Builder invocationBuilder = targetResource.request(...);
invocationBuilder.header("Authorization", accessToken.toAuthorizationHeader());
click below button to copy the code. By - oauth tutorial - oauth2 tutorial - team
Dealing with errors
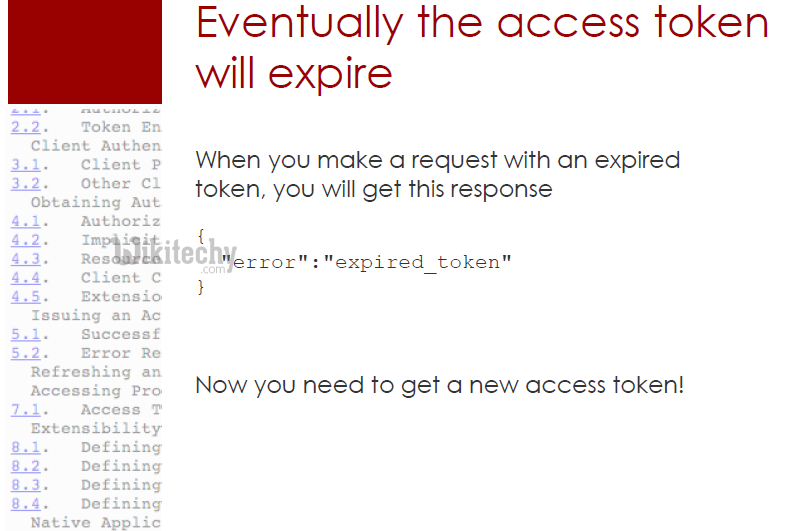
- If we get a 4xx HTTP status code check the WWW-Authenticate header whether request is failed due to an invalid or expired access token.
HTTP/1.1 401 Unauthorized
WWW-Authenticate: Bearer realm="example",
error="invalid_token",
error_description="The access token expired"
click below button to copy the code. By - oauth tutorial - oauth2 tutorial - team
The bearer specifies the following error codes:
- invalid_request is the request which was badly constructed.
- invalid_token is the provided access token which is invalid or has been expired.
- insufficient_scope is the provided scope which is valid, but it is not sufficient to perform the request.
- no error code No access token was provided with the request.
Bearer Token Errors:
import com.nimbusds.oauth2.sdk.token.*;
// Get the WWW-Authenticate header.
wwwAuthHeader = ...
// Parse it
BearerTokenError error = BearerTokenError.parse(wwwAuthHeader);
// Check the error code
if (error.equals(BearerTokenError.MISSING_TOKEN)) {
// Handle missing token...
} else if (error.equals(BearerTokenError.INVALID_REQUEST)) {
// Malformed request...
} else if (error.equals(BearerTokenError.INVALID_TOKEN)) {
// Refresh / obtain new token...
} else if (error.equals(BearerTokenError.INSUFFICIENT_SCOPE)) {
// Overstepped authorisation / obtain new token with required scope
}
click below button to copy the code. By - oauth tutorial - oauth2 tutorial - team
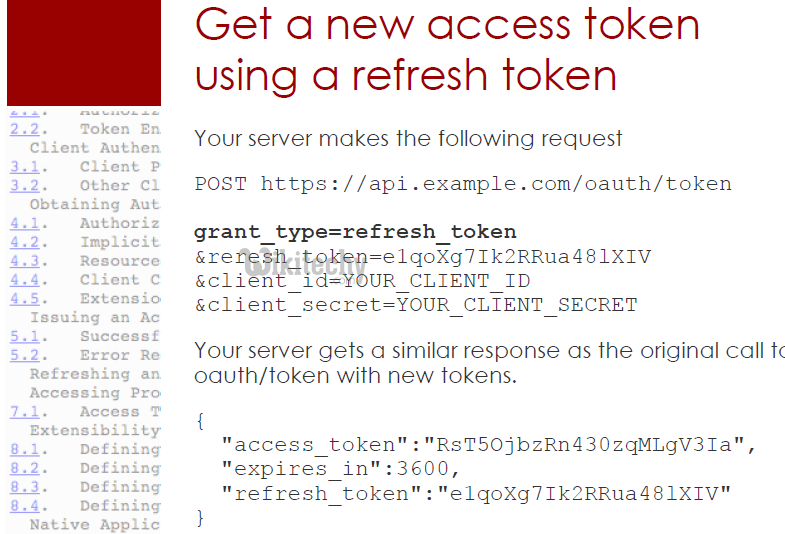
Accessing Resources - So you have an access token. Now what?