oauth tutorial - OAuth Terminology - oauth2 tutorial - oauth authentication
What is terminology in OAuth 2.0?
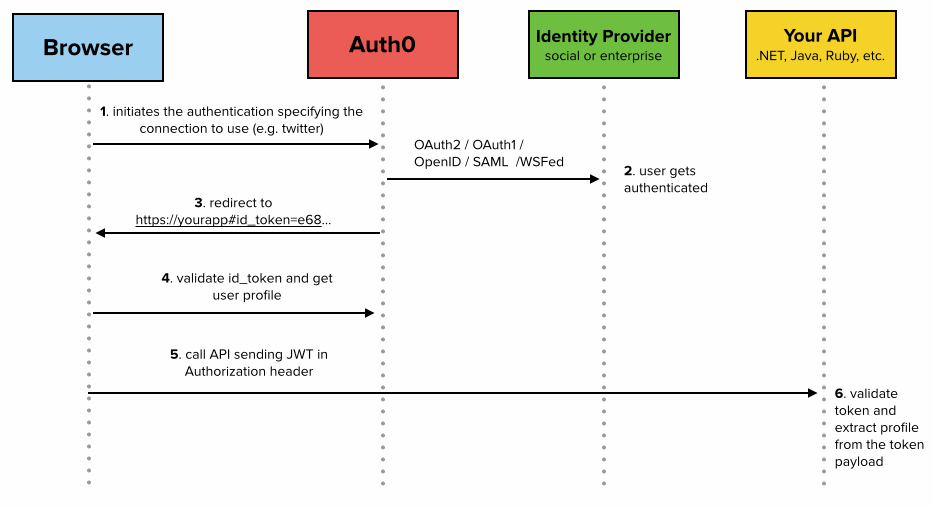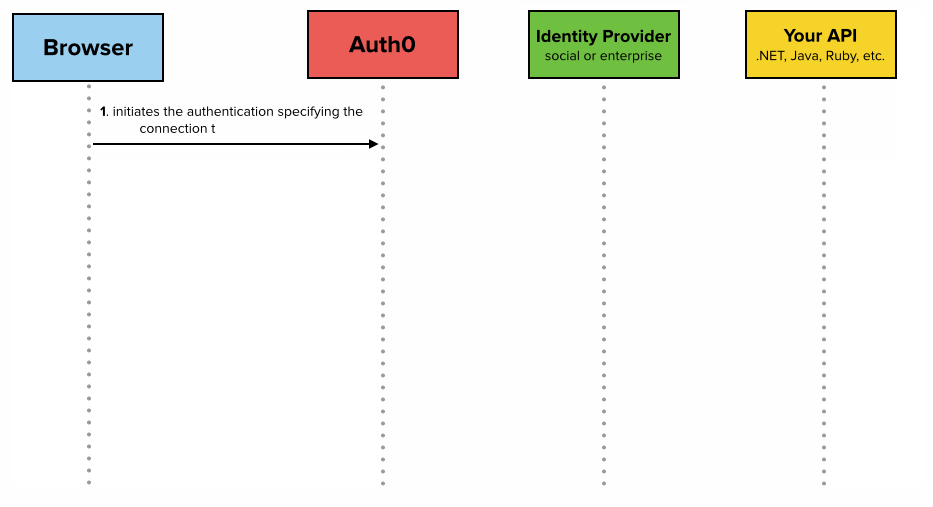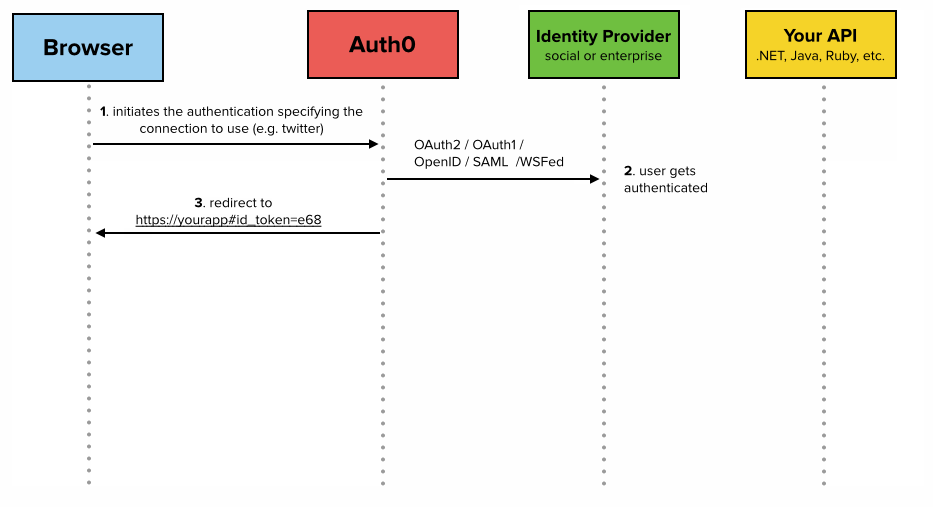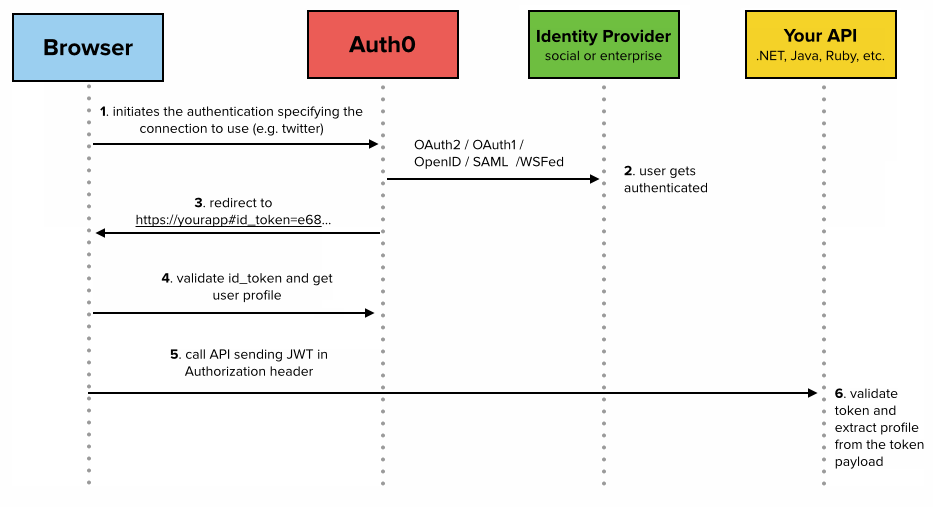
- Access token - A token which is used to access protected resources.
- Authorization code - An intermediary code generated when a user authorizes a client to access the protected resources. The client receives this code and exchanges it for an access code.
- Authorization server - A server issues access tokens after successfully authenticating a client and resource owner, and authorizing the request.
- Resource server - A server which is in front of the protected resources and is capable of accepting and responding to the protected resource requests using access tokens.
- Resource owner - The owner who authorizes an application to access their account.
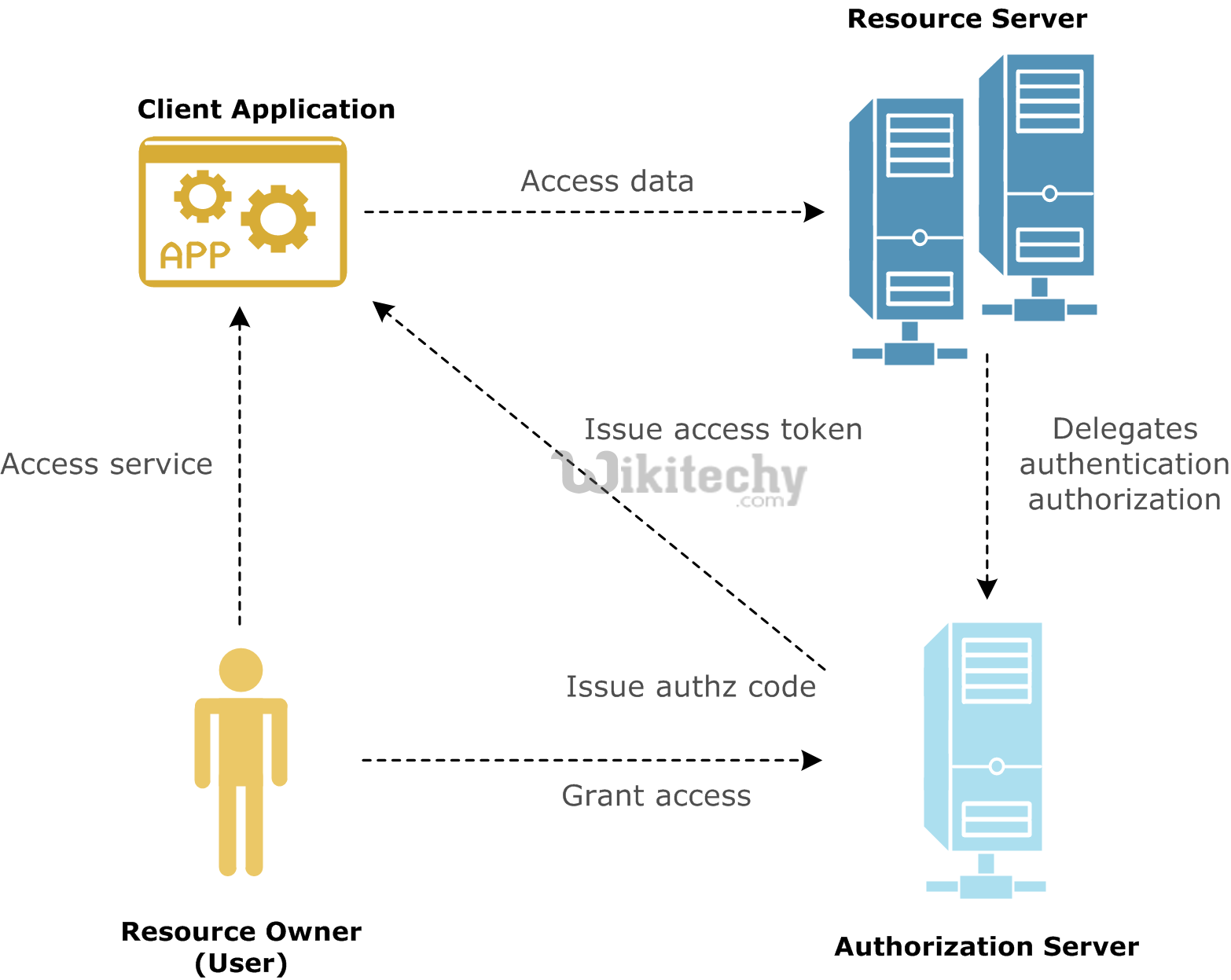
Learn OAuth - OAuth tutorial - OAuth Terminology - OAuth examples - OAuth programs
Authentication
- Authentication is a process of identifying an individual, which is based on the username and password of the user.
- Authentication knows that the user is the owner of the account on the web application and desktop computers.
- Authentication in the context of a user is accessing an application and also an application whether the current user is present or not.
- The Authentication protocol will also tell us the number of attributes about the user, such as a unique identifier and the email address
- Authentication is about the user and the presence of the user with the application, and is an internet-scale authentication protocol that needs to be able to do this across the network and security boundaries.
Federated Authentication
- In Federated Authentication, Many applications have their own username and passwords and applications depend on other services for verification of the user's identity.
- A federated identity management system provides a single access to multiple systems. This is known as federated authentication.
- A federated identity is the meaning of linking a person's electronic identity and attributes, which is stored across multiple distinct identity management systems.
- A federated identity is single sign-on (SSO), in which a user's single authentication token, is trusted across multiple IT systems or even organizations.
- SSO is a subset of federated identity management and it relates only to authentication and is based on the level of technical interoperability.
Authorization
- Authorization is the process of giving someone the permission to access the website.
- Hence, it needs the valid user's identification to check whether that user is authorized or not.
Delegated Authorization
- Delegated authorization is the process of giving one user credentials to another user to perform some actions based on the user.
- If an authorization mechanism provides an effective identity different from the validated identity of the user then it is called identity delegation authorization
- At the authorization level which provides the owner of the effective identity has authorized the owner of the validated identity to use his authorize identity
Roles
- OAuth 2.0 has four different types of roles and they are
- Resource Owner
- Client Application
- Resource Server
- Authentication Server
- The roles are illustrated in the diagram which is given below:
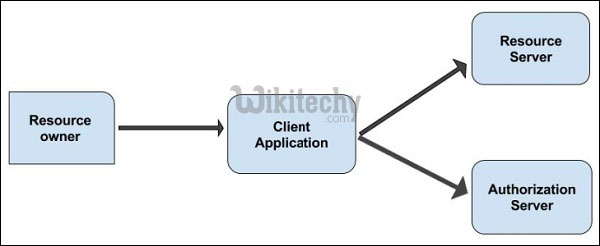
Learn OAuth - OAuth tutorial - OAuth Roles - OAuth examples - OAuth programs
Resource Owner
- The resource owner is a user who authorizes an application to access the account of the user.
- Resource owner is defined as an entity which has the ability to grant access to the user data hosted on the resource server.
- When the resource owner is a person, it is called as an end-user.
Client Application
- The client is the application that wants to access the user's account.
- Client is an application which makes protected resource requests to perform actions which is done based on the resource server
- Client application is authorized by the user and is validated by the API.
Resource Server
- The resource server hosts the protected user accounts and verifies the identity of the user and issues access tokens to the application.
- Resource server is an API server which can be used to access the user's information.
- Resource server has the capability of accepting and responding to the protected resource requests with the help of access tokens
Authentication Server
- The authentication server gets permission from the resource owner and distributes the access tokens to clients, to access protected resource hosted by the resource server.
- The authentication server authenticates to the authorization server and then, the client authenticates to the authorization server in the token endpoint.
- The authentication server flow is used by apps which are hosted on a secure server.
curl -H "Authorization: Bearer RsT5OjbzRn430zqMLgV3Ia" \
https://api.oauth2server.com/1/me
