Hack Instagram Account | Instagram Hack
What is Instagram ?
- Instagram is an online mobile photo-sharing, videosharing and social networking service, which enables its users to take pictures and videos and also to share them.
- The name “Instagram” is a combination of two words, they are “instant camera” and “telegram”.
- It is used to allow users to upload image content in their personal profiles, businesses to upload content visually and also build followers.
- Most popular mobile apps and best platform for photo contests and campaigns.
- Another feature with Instagram is the ability to Geotag your location and find users in the same area.
- Instagram was founded in 2010 by Stanford graduates Kevin Systorm and Mike Krieger.
- On October 6, 2010, Instagram was added to the Apple App Store.
- In April 2012, Instagram was added to Android.
- In late 2012, Instagram was purchased by Facebook for $1 billion.
What is Humen error hacking tool ?
- Phishing Tool for Advanced Instagram Copyright Infringement Attack. This tool is come under the Ethical hacking tutorial.
Other alternatives of Phishing Tool:
INFOSEC IQ - Phishing tool
- This tool includes a free Phishing Risk Test. It allows you to launch a simulated phishing campaign and receive your firm’s phish rate.
- You can also access full-scale phishing simulation tool, PhishSim, to run sophisticated simulations for your entire company.
- PhishSim contains a library of 1,000+ phishing templates, attachments and data entry landing pages. Templates are added weekly, allowing you to educate employees on the most topical phishing scams.

Learn Ethical Hacking - Ethical Hacking tutorial - INFOSEC IQ - Phishing tool - Ethical Hacking examples - Ethical Hacking programs
- Sign up for free account which gets you full access the tools and template. There is one condition which is you need to speak with an Infosec IQ representative for the ability to launch a free account.
Gophish
- Gophish is one of the best Ethical Hacking tool. This tool is open-source phishing platform, that gets it right. It is supported by most operating systems; installation is simple as downloading and extracting a ZIP folder.
- The Interface is simple and intuitive. Features are while limited and implemented carefully.
- Users can be easily added, or by bulk CSV importing. Email templates are easy for creation and modification (using variables allows for easy personalization), creating campaigns is a straightforward process, and reports are pleasant to look at and can be exported to CSV format with various levels of detail.

Learn Ethical Hacking - Ethical Hacking tutorial - Gophish - Ethical Hacking examples - Ethical Hacking programs
Simple Phishing Toolkit (sptoolkit)
- In this Phishing tool, the solution may lack in the GUI attractiveness department compared with some of the previous entries.
- There is an important feature that puts high on our list.
- It provides an opportunity to combine phishing tests and security awareness education.
- Moreover, there is a tracking feature for training completed people. Unfortunately, this tool has been abandoned in the year 2013. A new team is trying to give it a new life, but as of now, the documentation is scarce and scattered all over the internet, making realistic implementation in an enterprise environment a difficult task.

Learn Ethical Hacking - Ethical Hacking tutorial - Simple Phishing Toolkit - Ethical Hacking examples - Ethical Hacking programs
Read Also
King Phisher
- These tool features are plentiful, including the ability to run multiple campaigns simultaneously, and geo location of phished users, web cloning capabilities, etc.
- A separate template having templates for both messages and server pages. User interface is simpler.
- Installation and configuration are not simple one.
- This tool supported only on Linux, with additional installation and configuration steps required.

Learn Ethical Hacking - Ethical Hacking tutorial - King Phisher - Ethical Hacking examples - Ethical Hacking programs
Two alternatives to work on insta account hack :
- Method 1 : Using Pass Decrptor
- Method 2 : Using Kali Linux Humen Error Tool
Method 1 : Hack Instagram account using PASS DECRYPTOR
PASS DECRYPTOR is known worldwide for hacking Instagram accounts. This application was developed by hackers. It allows the password of any Instagram account to be displayed in clear text from a username, phone number or email. You only need 1 of the 3 pieces of information to hack the password.
PASS DECRYPTOR works on mobile, tablet and computer. It is able to bypass 2FA protections (double authentication factors).
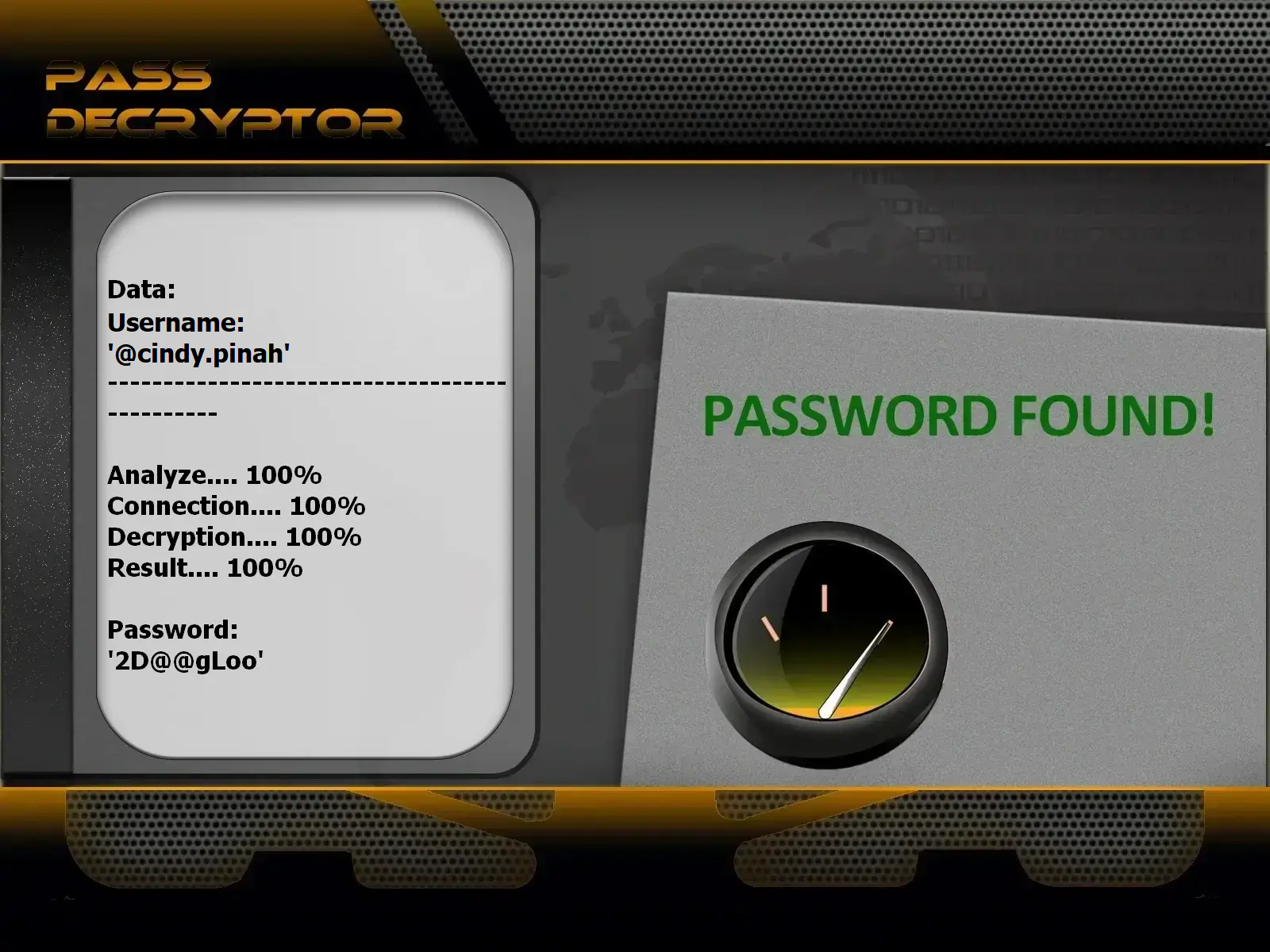
Get access to PASS DECRYPTOR from this link and hack INSTAGRAM password NOW:
Download Now
Method 2 : Instagram Hacking using Link:
Step 1:
- Open your Browser and download the Humen error tool from github.

Learn Ethical Hacking - Ethical Hacking tutorial - Open Browser - Ethical Hacking examples - Ethical Hacking programs
Step 2:
- Right click on the zip file then click extract here.

Learn Ethical Hacking - Ethical Hacking tutorial - Open the Extracted File - Ethical Hacking examples - Ethical Hacking programs
Step 3:
- Extracted file is ready then open the file.

Learn Ethical Hacking - Ethical Hacking tutorial - Open the Extracted File - Ethical Hacking examples - Ethical Hacking programs
Step 4:
- Open the Instagram folder.

Learn Ethical Hacking - Ethical Hacking tutorial - Open the Instagram Folder - Ethical Hacking examples - Ethical Hacking programs
Step 5:
- Delete this image file and insert victims Instagram image.

Learn Ethical Hacking - Ethical Hacking tutorial - Insert Victims Image - Ethical Hacking examples - Ethical Hacking programs
Step 6:
- Paste Instagram profile image and also rename the picture as image.jpg

Learn Ethical Hacking - Ethical Hacking tutorial - Paste Profile Image - Ethical Hacking examples - Ethical Hacking programs
Step 7:
- Right click the index.html and open with text editor.

Learn Ethical Hacking - Ethical Hacking tutorial - Click Index HTML File - Ethical Hacking examples - Ethical Hacking programs
Read Also
Step 8:
- The file of index.html will appear.

Learn Ethical Hacking - Ethical Hacking tutorial - Index HTML - Ethical Hacking examples - Ethical Hacking programs
Step 9:
- Click ctrl+f then find window will pop up and type Target circle image then click find.

Learn Ethical Hacking - Ethical Hacking tutorial - Type Victim Name - Ethical Hacking examples - Ethical Hacking programs
Step 10:
- Replace Target circle image to victim profile image name and save.

Learn Ethical Hacking - Ethical Hacking tutorial - Replace Target Circle Image - Ethical Hacking examples - Ethical Hacking programs
Step 11:
- Put image name as image.jpg

Learn Ethical Hacking - Ethical Hacking tutorial - Put Image Name - Ethical Hacking examples - Ethical Hacking programs
Step 12:
- Click ctrl+f and type (victim Name) then click find button.

Learn Ethical Hacking - Ethical Hacking tutorial - Type Victim Name - Ethical Hacking examples - Ethical Hacking programs
Step 13:
- Replace the (Victim Name) to victims Instagram name.

Learn Ethical Hacking - Ethical Hacking tutorial - Replace Victim Name - Ethical Hacking examples - Ethical Hacking programs
Step 14:
- Put Instagram id name.

Learn Ethical Hacking - Ethical Hacking tutorial - Instagram ID - Ethical Hacking examples - Ethical Hacking programs
Step 15:
- Open Terminal.

Learn Ethical Hacking - Ethical Hacking tutorial - Open Terminal - Ethical Hacking examples - Ethical Hacking programs
Step 16:
- Type the command cd Downloads and then type ls to list the files. Hit enter then type cd HumenError-master

Learn Ethical Hacking - Ethical Hacking tutorial - Type the Command HumanError Master - Ethical Hacking examples - Ethical Hacking programs
Read Also
Step 17:
- Access a tool, then the tool is successfully running then put 1 for Instagram hacking.

Learn Ethical Hacking - Ethical Hacking tutorial - Put One for Instagram Hacking - Ethical Hacking examples - Ethical Hacking programs
Step 18:
- Choose 1 and hit enter.

Learn Ethical Hacking - Ethical Hacking tutorial - Choose Attack One - Ethical Hacking examples - Ethical Hacking programs
Step 19:
- Choose 2 for port forwarding option then hit enter.

Learn Ethical Hacking - Ethical Hacking tutorial - Choose Two for Port Forwarding Option - Ethical Hacking examples - Ethical Hacking programs
Step 20:
- Here the Link is ready which is shown here. Copy the link and send to the victim.

Learn Ethical Hacking - Ethical Hacking tutorial - Link - Ethical Hacking examples - Ethical Hacking programs
Step 21:
- Open the link in browser.

Learn Ethical Hacking - Ethical Hacking tutorial - Open the Link in Browser - Ethical Hacking examples - Ethical Hacking programs
Step 22:
- The page is load in victim’s browser. Victim will click the verify account then next page will open.

Learn Ethical Hacking - Ethical Hacking tutorial - Click Verify Account - Ethical Hacking examples - Ethical Hacking programs
Step 23:
- This page is Instagram credential page. Victim will put D.O.B and email address and password.

Learn Ethical Hacking - Ethical Hacking tutorial - Instagram Credential Page - Ethical Hacking examples - Ethical Hacking programs
Step 24:
- Click Confirm E-mail.

Learn Ethical Hacking - Ethical Hacking tutorial - Confirm Email - Ethical Hacking examples - Ethical Hacking programs
Step 25:
- This is for Gmail credential page, here victim will enter email id and password then finally click submit button.

Learn Ethical Hacking - Ethical Hacking tutorial - Submit Email and Password - Ethical Hacking examples - Ethical Hacking programs
Step 26:
- This is the final pop up for victim side.

Learn Ethical Hacking - Ethical Hacking tutorial - Copyright Notice - Ethical Hacking examples - Ethical Hacking programs
Step 27:
- Finally, got the Instagram and Gmail credentials.

Learn Ethical Hacking - Ethical Hacking tutorial - Got Instagram Email Credentials - Ethical Hacking examples - Ethical Hacking programs
Step 28:
- If you want to learn about Ethical Hacking Course , you can refer the following links Ethical Hacking Training in Chennai, Ethical Hacking tutorial, Hacking Course , Ethical Hacking Training , Learn Ethical Hacking.
