Cyber Security Digital Signature
Cyber Security Digital Signature
- A digital signature is a mathematical technique which validates the authenticity and integrity of a message, software or digital documents the digital signature offers far more inherent security and intended to solve the problem of tampering and impersonation in digital communications.
- The digital signatures are different from other electronic signatures not only in terms of process and result, but also it makes digital signatures more serviceable for legal purposes.
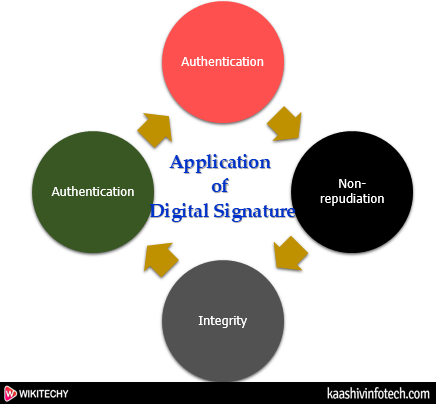
Application of Digital Signature
Cyber Security Digital Signature
- The important reason to implement digital signature to communication is:
- Authentication
- Non-repudiation
- Integrity
Authentication
- In the digital signature, authentication helps to authenticate the sources of messages.
Non-repudiation
- Non-repudiation means assurance of something that cannot be denied.
Integrity
- Integrity ensures that the message is real, accurate and safeguards from unauthorized user modification during the transmission.
Algorithms in Digital Signature
A digital signature consists of three algorithms:
Key generation algorithm
- This algorithm provides the private key and its corresponding public key.
Signing algorithm
- A signing algorithm produces a signature for the document.
Signature verifying algorithm
- A signature verifying algorithm either accepts or rejects the document's authenticity.
How Digital Signatures Work ?
- By the use of a public key algorithm, such as RSA, one can generate two keys that are mathematically linked- one is a private key, and another is a public key.
- There is only one way to decrypt that document is with the use of signer's public key.
- This technology requires all the parties to trust that the individual who creates the signature has been able to keep their private key secret.
- The steps which are followed in creating a digital signature are:
- Select a file to be digitally signed.
- The hash value of the message or file content is calculated. This message or file content is encrypted by using a private key of a sender to form the digital signature.
- The receiver decrypts the digital signature by using a public key of a sender.
- The receiver now has the message or file content and can compute it.
- Comparing these computed message or file content with the original computed message.
Read Also
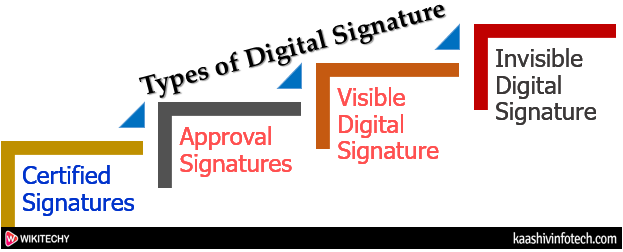
Types of Digital Signature
Different document processing platform supports different types of digital signature. They are described below:
Digital Signature Types
Certified Signatures
- Certified signature contains the name of the document signer and the certificate issuer which indicate the authorship and authenticity of the document.
Approval Signatures
- The approval digital signatures on a document can be used in the organization's business workflow. The approval signatures to include details such as an image of our physical signature, location, date, and official seal.
Visible Digital Signature
- The visible digital signature allows a user to sign a single document digitally.
Invisible Digital Signature
- The invisible digital signatures carry a visual indication of a blue ribbon within a document in the taskbar.
