What is Cyber Security ?
What is Cyber Security ?
- Cyber Security - It is about people, processes, and technologies working together to encompass the full range of threat reduction, vulnerability reduction, etc."
- It is made up of two words one is cyber and other is security. Cyber is related to the technology which contains systems, network and programs or data.
- It is the form of technologies, processes, and practices designed to protect networks, devices, programs, and data from attack, theft, damage, modification or unauthorized access. It may also be referred to as information technology security.
- Cybersecurity is a critical function and needed insurance of many businesses.
- Cyber security is the practice of defending :
- Computers,
- Servers,
- Mobile devices,
- Electronic systems,
- Networks, and data from Malicious Attacks.
- It is also known as Information technology security or electronic information security.
- The term applies in a variety of contexts, from business to mobile computing, and can be divided into a few common categories.
Information Technology Security
Network security
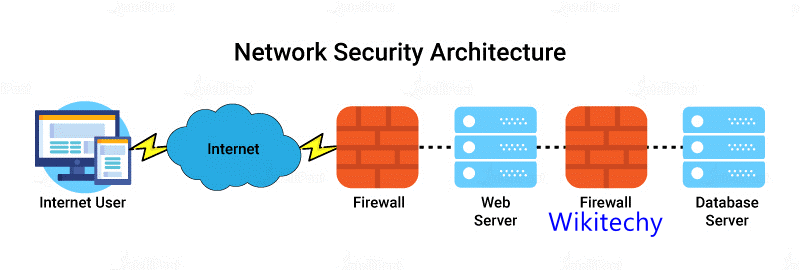
- Network is the practice of securing a computer network from intruders, whether targeted attackers or opportunistic malware.
- Network security is any activity designed to protect the usability and integrity of your network and data.
- It includes both hardware and software technologies
- It targets a variety of threats
- It stops them from entering or spreading on your network
- Effective network security manages access to the network
Application security
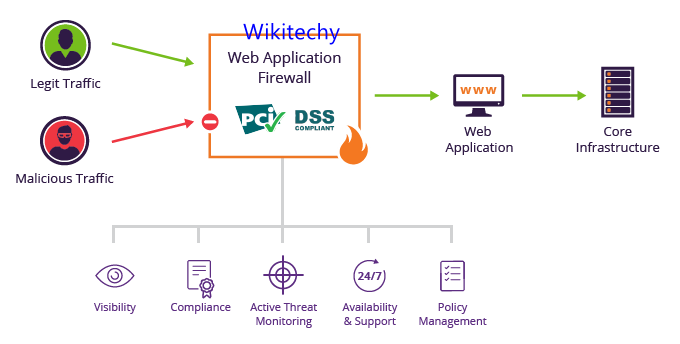
- Application security focuses on keeping software and devices free of threats.
- Application security describes security measures at the application level that aim to prevent data or code within the app from being stolen or hijacked.
- It encompasses the security considerations that happen during application development and design.
- It also involves systems and approaches to protect apps after they get deployed.
Information security
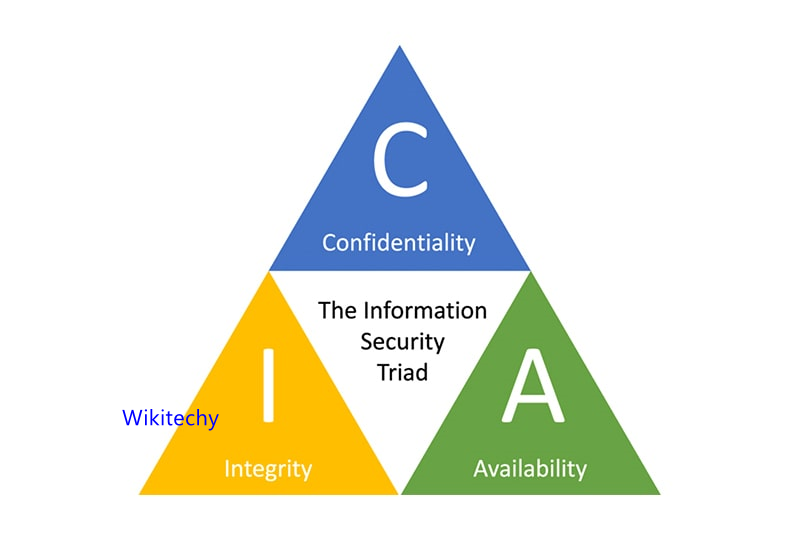
- Information Security is basically the practice of preventing Unauthorized access to :
- Disclosure,
- Disruption,
- Modification,
- Inspection,
- Recording or destruction of information.
- Information can be physical or electronic one.
- Information can be anything like Your details or we can say your profile on social media, your data in mobile phone, your biometrics etc.
Disaster recovery and business continuity
- Disaster recovery and business continuity define how an organization responds to a cyber-security incident or any other event that causes the loss of operations or data.
- Disaster recovery policies dictate how the organization restores its operations and information to return to the same operating capacity as before the event.
- Business continuity is the plan of the organization to falls back on while trying to operate without certain resources.
Why is Cyber Security Important ?
- A data can be sensitive information, whether that intellectual property, financial data, personal information, or other types of data for which unauthorized access or exposure have negative consequences. Cyber-attack is an international concern and has given many concerns hacks and other security attacks could endanger the global economy.
- Organizations transmit sensitive data across networks and to other devices in the course of doing businesses, and cybersecurity describes to protect information and the systems used to process or store it.
This tutorial provides basic and advanced concepts of Cyber Security technology.

Cyber Security
